Kalpa
Kalpa
Cybersecurity Posture Management Software
Cybersecurity Posture Management Software
01
Team
As a team, you can communicate internally regarding all aspects of your organisation's cybersecurity posture. Each team member will have a profile, with a list of tasks and responsibilities.



Brooklyn Simmons
Project Manager

Darrell Steward
President of Sales

Savannah Nguyen
Marketing Coordinator



Brooklyn Simmons
Project Manager

Darrell Steward
President of Sales

Savannah Nguyen
Marketing Coordinator
02
Task & Events
Security managers can assign tasks and responsibilities to their team members. Each event may be accepted or rejected, and all communication is logged for observability and transparency.
Security managers can assign tasks and responsibilities to their team members. Each event may be accepted or rejected, and all communication is logged for observability and transparency.
Asset is rejected
Asset Rejected
3 weeks ago
Asset is shared by Jack
Asset Assigned
2 weeks ago
Asset is created
Asset Created
2 weeks ago
03
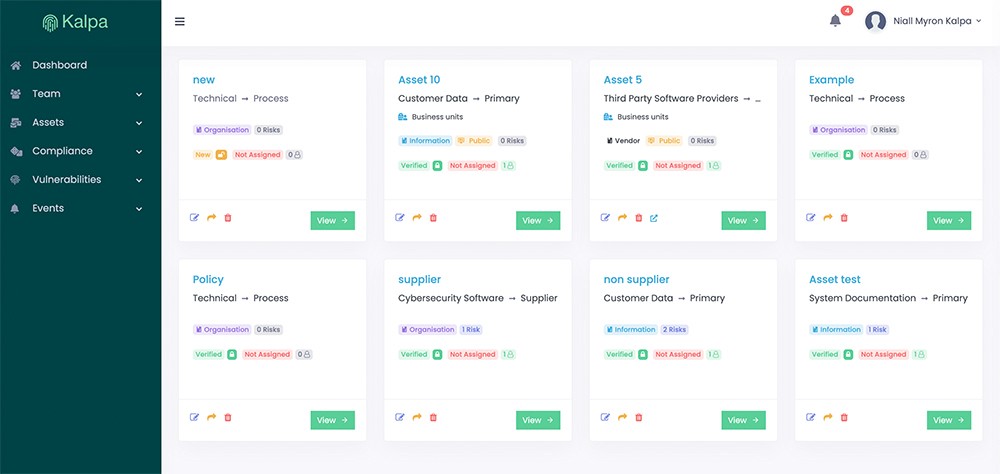
Asset Inventory
An asset is anything that adds value to your organisation. Kalpa allows you to extend the management of your information asstes, by helping you track organisation assets like people, processes, 3rd party vendors, business units, and others.

Github code
Confidential
Physical
Verified
View
Asset
Confidential
Digital
Database
Assigned
3
Blocked
View
Github code
Confidential
Physical
Verified
View
Asset
Confidential
Digital
Database
Assigned
3
Blocked
View

Github code
Confidential
Physical
Verified
View
Asset
Confidential
Digital
Database
Assigned
3
Blocked
View
Github code
Confidential
Physical
Verified
View
Asset
Confidential
Digital
Database
Assigned
3
Blocked
View
04
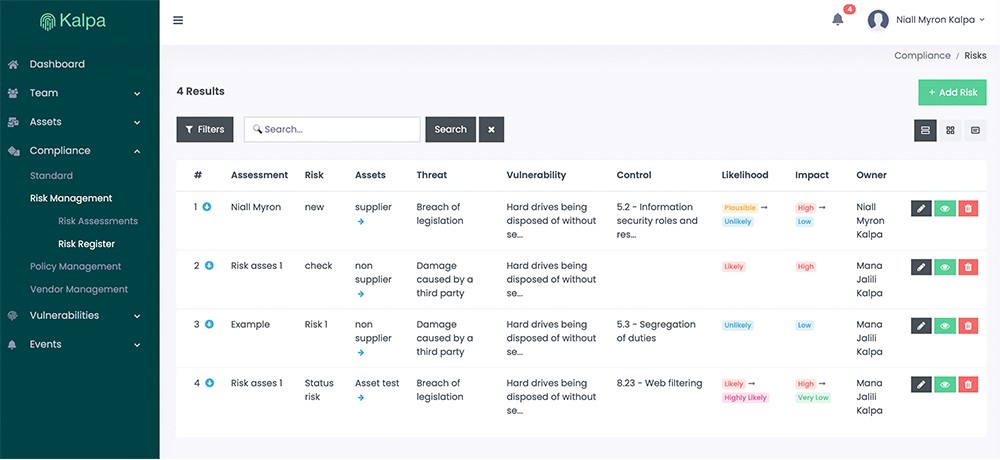
Risk Assessment
At Kalpa we believe asset based risk assessments are the most effective way to manage risk. The Kalpa platform enables your security team to scrutinise all of your assets by assigning threats & vulnerabilities, defining risk scores, implementing controls, and then managing the risk through associated processes and procedures.


Likelihood
Highly Unlikely
Impact
Very High
Likelihood
Highly Unlikely
Impact
Very High


Likelihood
Highly Unlikely
Impact
Very High
Likelihood
Highly Unlikely
Impact
Very High
05
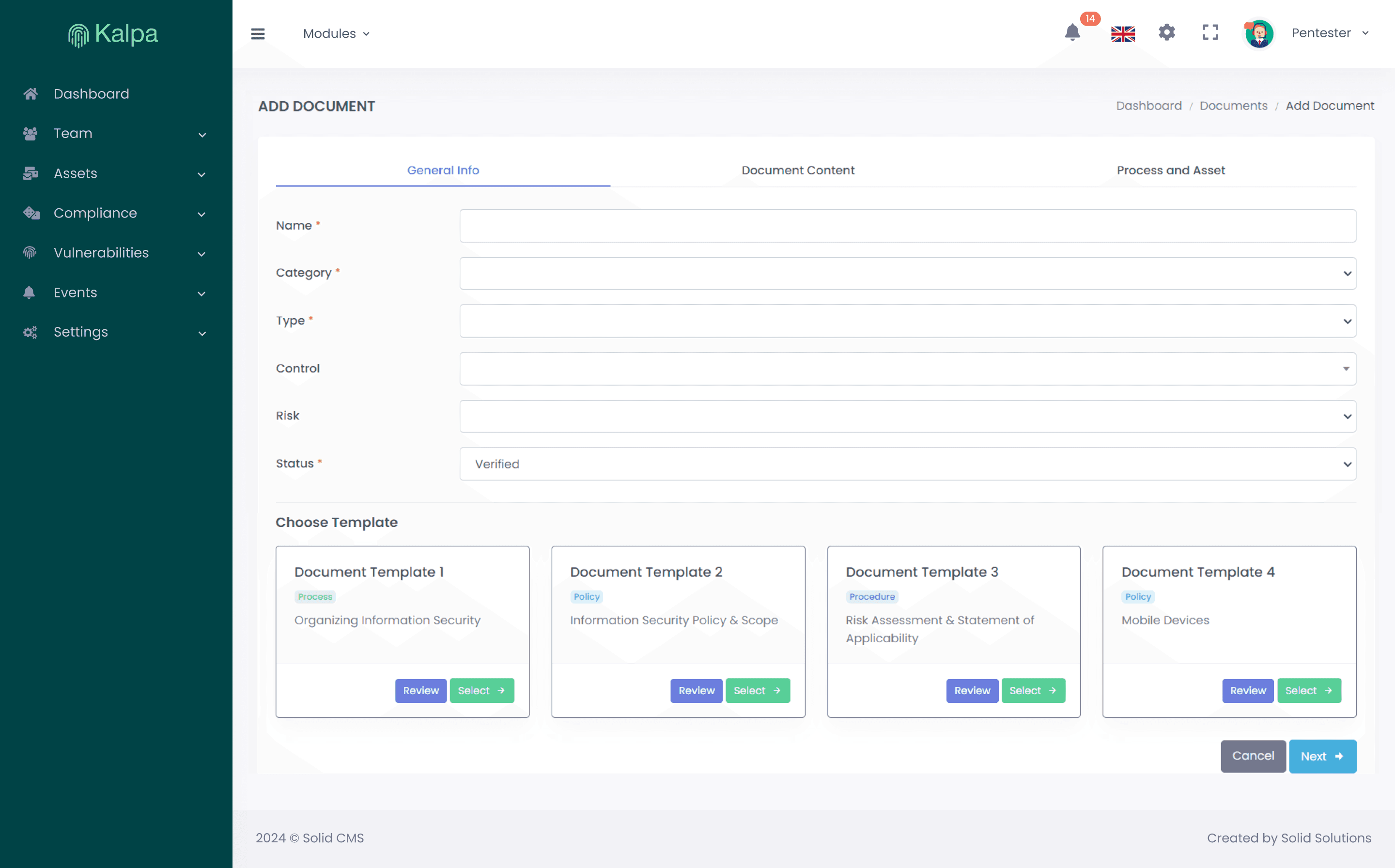
Policies & Processes
When applying the necessary controls during risk assessments, Kalpa allows you to easily create, manage and maintain documents relating to the various policies, processes, and procedures necessary in ISO27001.

kalpa.com
kalpa.com

kalpa.com

kalpa.com

06
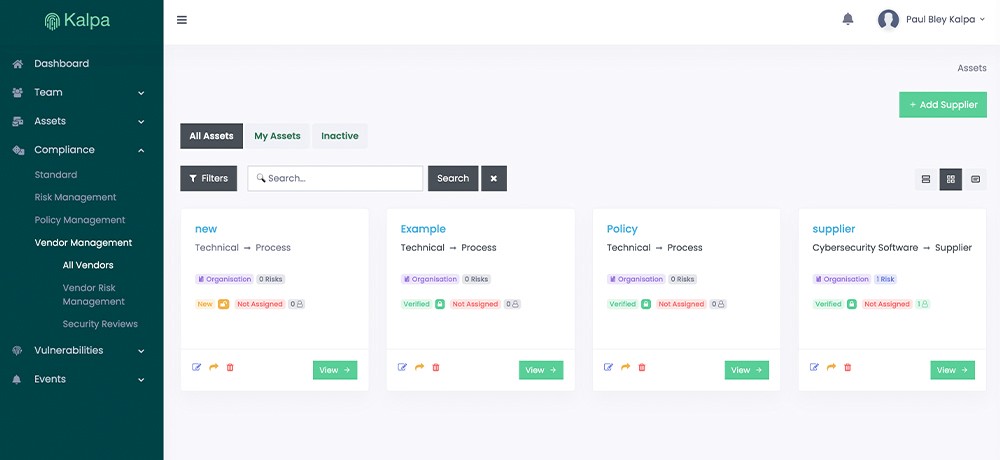
Vendor Management
Kalpa allows you to identify all of your 3rd party vendors. You can track and manage those vendors, automate the security questionnaire process, and then generate vendor risk scores based on the results.

kalpa.com
kalpa.com

kalpa.com

kalpa.com

07
Vulnerability Management
Kalpa acts as a unified API to accept vulnerability data from various sources. You can track and manage all vulnerabilities, automate the vulnerability to risk process, and easily accept vulnerability reports with a vulnerability disclosure program.

kalpa.com
kalpa.com

kalpa.com

kalpa.com

08
Breach Simulation Management
Security teams can test their readiness with simulated breach scenarios. Kalpa automatically creates breaches based on either randomness or user inputs. Security teams are monitored on how they respond to each breach scenario with various KPI's.

kalpa.com
kalpa.com

kalpa.com

kalpa.com

Kalpa
Cybersecurity Posture Management Software
01
Team
As a team, you can communicate internally regarding all aspects of your organisation's cybersecurity posture. Each team member will have a profile, with a list of tasks and responsibilities.



Brooklyn Simmons
Project Manager

Darrell Steward
President of Sales

Savannah Nguyen
Marketing Coordinator



Brooklyn Simmons
Project Manager

Darrell Steward
President of Sales

Savannah Nguyen
Marketing Coordinator
02
Task & Events
Security managers can assign tasks and responsibilities to their team members. Each event may be accepted or rejected, and all communication is logged for observability and transparency.
Asset is rejected
Asset Rejected
3 weeks ago
Asset is shared by Jack
Asset Assigned
2 weeks ago
Asset is created
Asset Created
2 weeks ago
03
Asset Inventory
An asset is anything that adds value to your organisation. Paradoxically, these assets are also liabilities, and must be properly tracked and maintained in order to ensure the security of your organisation.

Github code
Confidential
Physical
Verified
View
Asset
Confidential
Digital
Database
Assigned
3
Blocked
View

Github code
Confidential
Physical
Verified
View
Asset
Confidential
Digital
Database
Assigned
3
Blocked
View
04
Risk Assessment
At Kalpa we believe asset based risk assessments are the most effective way to manage risk. The Kalpa platform enables your security team to scrutinise all of your assets by assigning threats & vulnerabilities, defining risk scores, implementing controls, and then managing the risk through associated processes and procedures.

Impact
Very High

Likelihood
Highly Unlikely

Impact
Very High

Likelihood
Highly Unlikely
05
Policies & Processes
When applying the necessary controls during risk assessments, Kalpa allows you to easily create, manage and maintain documents relating to the various policies, processes, and procedures necessary in ISO27001.

kalpa.com


kalpa.com

06
Vendor Management
Kalpa allows you to identify all of your 3rd party vendors. You can track and manage those vendors, automate the security questionnaire process, and then generate vendor risk scores based on the results.

kalpa.com


kalpa.com

07
Vulnerability Management
Kalpa acts as a unified API to accept vulnerability data from various sources. You can track and manage all vulnerabilities, automate the vulnerability to risk process, and easily accept vulnerability reports with a vulnerability disclosure program.

kalpa.com


kalpa.com

08
Breach Simulation Management
Security teams can test their readiness with simulated breach scenarios. Kalpa automatically creates breaches based on either randomness or user inputs. Security teams are monitored on how they respond to each breach scenario with various KPI's.

kalpa.com


kalpa.com

Navigation
Contact Us
©2024 All right reserved
Privacy Policy
Terms of Use
Cookies
Navigation
Contact Us
©2024 All right reserved
Privacy Policy
Terms of Use
Cookies